If you own a WordPress website in 2025 — whether it’s for your barbershop, bakery, photography studio, coaching business, or any local service — you’re probably relying on it more than ever. It’s where customers find you, trust you, book you, and judge your professionalism.
But here’s the truth most people never hear:
WordPress is secure, but only if you secure it.
Hackers rarely break into websites through “Hollywood-style hacking.”
They break in because most business owners never harden their WordPress installation. And nothing exposes a site faster than a default wp-config.php file and an unprotected .htaccess file.
The good news?
You can dramatically enhance your WordPress security in just a few minutes — without being a developer, without understanding code, and without installing a dozen plugins.
This guide walks you through exactly what to add to your wp-config.php and .htaccess files, explains why these changes matter, and helps you lock down your website the same way agencies and security professionals do.
Let’s get started.
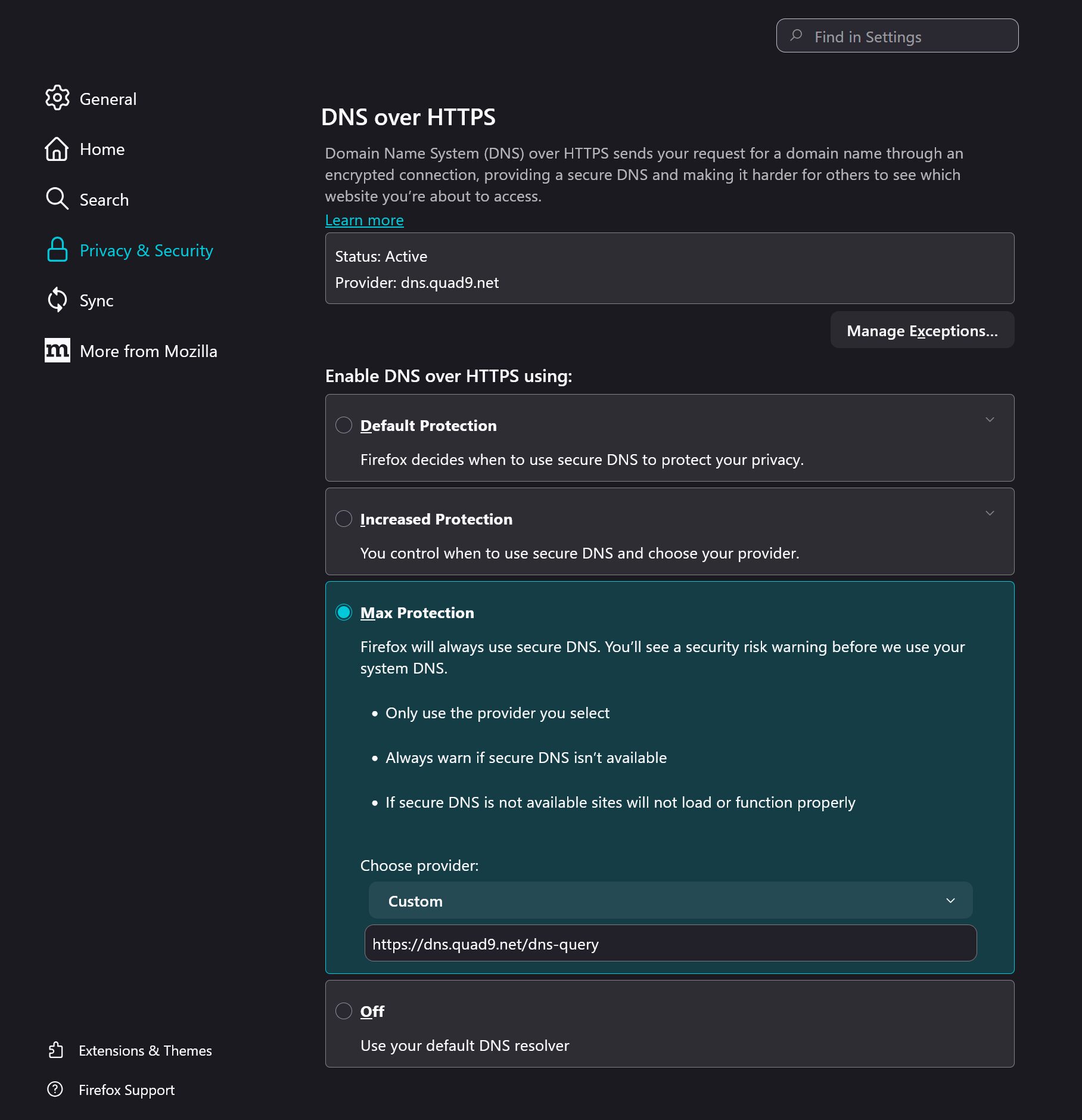
Why wp-config.php and .htaccess Matter for WordPress Security
Before we copy anything, it helps to understand what these files actually do — in simple, real-world language.
The wp-config.php file is the brain of your WordPress installation. It controls how WordPress behaves, how much memory it can use, whether errors show publicly, and whether hackers can edit code inside your dashboard. A few extra lines in this file can close common security gaps instantly.
The .htaccess file, on the other hand, sits at the front door of your website. It tells your server what to allow, what to block, and what to shut down before WordPress even loads. If wp-config.php is your master key, .htaccess is the lock on the shop door.
Most website owners never touch these files — not because the process is difficult, but because nobody walks them through it in a way that feels approachable.
This is that guide.
Hardening Your wp-config.php — The Powerful Changes That Boost WordPress Security
The wp-config.php file is located inside your public_html (or main WordPress folder). All you need to do is open it in your hosting File Manager, scroll down until you see the line:
/* That's all, stop editing! Happy publishing. */…and paste the following block right above it:
define( 'WP_DEBUG', false );
define( 'WP_DEBUG_DISPLAY', false );
@ini_set( 'display_errors', 0 );
/** Security & Performance – Final 2025–2026 */
define('DISALLOW_FILE_EDIT', true);
// define('DISALLOW_FILE_MODS', true); // optional security hardening
define('FORCE_SSL_ADMIN', true);
define('WP_POST_REVISIONS', 5);
define('AUTOSAVE_INTERVAL', 300);
define('EMPTY_TRASH_DAYS', 7);
define('WP_MEMORY_LIMIT', '256M');
define('WP_MAX_MEMORY_LIMIT', '512M');
define('WP_DISABLE_FATAL_ERROR_HANDLER', true);
define('CONCATENATE_SCRIPTS', false);
// define('WP_CACHE', true); // enable if Redis/LSCache is installed
// define('DISABLE_WP_CRON', true); // enable only if server cron is set
@ini_set('upload_max_filesize', '128M');
@ini_set('post_max_size', '128M');
@ini_set('max_execution_time', '300');
@ini_set('max_input_time', '300');If copying and pasting a code block feels intimidating, think of it like adding a new setting to your phone. You don’t need to understand the numbers — you just need them in the right place.
So what do these lines actually do for your WordPress security?
They turn off public error display (hackers love these because they reveal sensitive server details), block theme and plugin code editing inside the dashboard (a common attack route), force secure HTTPS login, prevent database bloat, increase memory limits, and improve upload and execution settings so things run more smoothly.
With one paste, your WordPress becomes cleaner, faster, and much harder to exploit.
Hardening Your .htaccess — The Server-Level Shield Your Site Has Been Missing
Your .htaccess file is even more important for WordPress security than most people realize. This is the file that controls how your server behaves before WordPress loads. It can block bots, stop malicious scripts, enforce HTTPS, deny access to backup files, and completely shut down certain attack methods.
You’ll find it in the same folder as wp-config.php. Open it, and look for:
# BEGIN WordPress…and paste the following block right above it:
# ===================================================================
# WordPress Ultimate .htaccess 2025 – Elementor + WP Rocket Safe
# Copy-paste ready – works on Apache & LiteSpeed (caching left enabled)
# ===================================================================
# -------------------------------
# EITHER USE 1A or 1B - DO NOT USE BOTH
# 1A. Force HTTPS + NO-WWW (safe & universal)
# -------------------------------
<IfModule mod_rewrite.c>
RewriteEngine On
# Force HTTPS
RewriteCond %{HTTPS} off
RewriteRule ^ https://%{HTTP_HOST}%{REQUEST_URI} [R=301,L]
# Remove www
RewriteCond %{HTTP_HOST} ^www\.(.*)$ [NC]
RewriteRule ^ https://%1%{REQUEST_URI} [R=301,L]
</IfModule>
# -------------------------------
# 1B. Force HTTPS + WWW (safe & universal)
# -------------------------------
<IfModule mod_rewrite.c>
RewriteEngine On
# Force HTTPS
RewriteCond %{HTTPS} off
RewriteRule ^ https://%{HTTP_HOST}%{REQUEST_URI} [R=301,L]
# Add www if missing
RewriteCond %{HTTP_HOST} !^www\. [NC]
RewriteRule ^ https://www.%{HTTP_HOST}%{REQUEST_URI} [R=301,L]
</IfModule>
# -------------------------------
# 2. Basic directory & file protection
# -------------------------------
Options -Indexes
# Block direct access to sensitive files
<FilesMatch "(wp-config\.php|\.htaccess|readme\.html|license\.txt|xmlrpc\.php)">
Require all denied
</FilesMatch>
# Block backup/temporary files
<FilesMatch "\.(bak|old|dist|sql|swp|swo|~|\.log)$">
Require all denied
</FilesMatch>
# -------------------------------
# 3. Block PHP execution in uploads
# -------------------------------
<IfModule mod_rewrite.c>
RewriteRule ^wp-content/uploads/.*\.(php|phtml|php\d|pl|py|jsp|asp|sh|cgi)$ - [F,L]
</IfModule>
# -------------------------------
# 4. Block common attack patterns
# -------------------------------
<IfModule mod_rewrite.c>
RewriteCond %{QUERY_STRING} (\.\./|<script|mosConfig|base64_decode.*\(.*\)) [NC]
RewriteRule ^ - [F,L]
# Stop author scanning
RewriteCond %{QUERY_STRING} ^author=\d+ [NC]
RewriteRule ^ - [F,L]
</IfModule>
# -------------------------------
# 5. Block bad bots / scanners
# -------------------------------
SetEnvIfNoCase User-Agent "(libwww-perl|python|sqlmap|nmap|nikto|acunetix|zmEu|MJ12bot|AhrefsBot|SemrushBot|Xenu)" bad_bot
<IfModule mod_authz_core.c>
<RequireAll>
Require all granted
Require not env bad_bot
</RequireAll>
</IfModule>
# Fallback for older Apache
<IfModule !mod_authz_core.c>
Order allow,deny
Allow from all
Deny from env=bad_bot
</IfModule>
# -------------------------------
# 6. Security headers – A+ SSLLabs & Elementor/WP Rocket compatible
# -------------------------------
<IfModule mod_headers.c>
Header always set X-Content-Type-Options "nosniff"
Header always set X-XSS-Protection "1; mode=block"
Header always set X-Frame-Options "SAMEORIGIN"
Header always set Referrer-Policy "strict-origin-when-cross-origin"
Header always set Permissions-Policy "geolocation=(), microphone=(), camera=()"
Header always set Strict-Transport-Security "max-age=31536000; includeSubDomains; preload"
# Gutenberg + Elementor + most plugins compatible CSP
# Header always set Content-Security-Policy "default-src 'self' https:; script-src 'self' 'unsafe-inline' 'unsafe-eval' https:; style-src 'self' 'unsafe-inline' https:; img-src 'self' data: https: blob:; font-src 'self' https: data:; connect-src 'self' https:; media-src 'self' https:; object-src 'none'; frame-src 'self' https:; child-src 'self' https:; frame-ancestors 'self';"
</IfModule>
# -------------------------------
# 7. WordPress core rules – DO NOT TOUCH
# -------------------------------
# BEGIN WordPress
# The directives (lines) between "BEGIN WordPress" and "END WordPress" are
# dynamically generated, and should only be modified via WordPress filters.
# Any changes to the directives between these markers will be overwritten.
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteRule .* - [E=HTTP_AUTHORIZATION:%{HTTP:Authorization}]
RewriteBase /
RewriteRule ^index\.php$ - [L]
RewriteCond %{REQUEST_FILENAME} !-f
RewriteCond %{REQUEST_FILENAME} !-d
RewriteRule . /index.php [L]
</IfModule>
# END WordPress
# ===================================================================
# Ready. Save & upload. Works perfectly with WP Rocket + Elementor.
# ===================================================================
PS: Make Sure to put either 1A or 1B – Placing both will break your website!
Your .htaccess hardening rules include sections for:
- Forcing all traffic to HTTPS
- Choosing www or non-www (use only ONE version)
- Blocking dangerous file access
- Preventing PHP execution inside uploads
- Blocking suspicious URL patterns
- Blocking malicious bots and scanners
- Adding modern browser security headers
- Leaving WordPress core rules untouched
This is professional-grade protection. The beauty is that you don’t need to write a single line — just paste the block you already created above the WordPress section.
Once you save the file, your site instantly gains multiple layers of protection that most small websites never have.
Why These Two Files Improve WordPress Security More Than Most Plugins
Many people install a bunch of security plugins hoping it will protect them. But plugins operate inside WordPress, which means attackers can still reach them.
Hardening wp-config.php and .htaccess works differently.
- It stops attacks before they reach WordPress
- It blocks malicious file execution
- It prevents hackers from viewing error output
- It protects your server environment
- It locks down sensitive files
- It reduces the attack surface dramatically
Think of it this way:
Security plugins are like alarms.
wp-config.php and .htaccess hardening is like steel doors.
You should have both — but one works deeper and protects earlier.
The Real Reason Small Business Sites Get Hacked
It’s rarely because a hacker “chose” you.
It’s because your site was easy.
Automated scripts scan the internet 24/7 for:
- Open directories
- Unsecured uploads folders
- Exposed error logs
- Files that should be hidden
- PHP files inside media folders
- Weak configuration options
By hardening your wp-config.php and .htaccess, you close these doors.
Hackers don’t spend time breaking into locked houses. They move on to the next easy target.
This is why the simple steps in this guide can protect your site more than any plugin alone ever will.
You may also be interested in Ultimate Firefox Hardening 2025: How to Make Firefox Private and Secure From the Start
Additional Ways to Strengthen Your WordPress Security (Non-Technical)
Once you’ve hardened your wp-config.php and .htaccess files, you’ve already done more than 90% of WordPress users. But a few extra habits will make your security even stronger:
- Keep plugins and themes updated – Outdated plugins are the #1 cause of hacks.
- Delete plugins you aren’t using – Less code = fewer vulnerabilities.
- Use a reputable security plugin – WP Cerber, Solid Security, or Wordfence.
- Enable 2FA for admin logins – A 6-digit code stops password guessing attacks.
- Use proper hosting – Sometimes the hosting is the weakest link.
- Take daily backups – One-click restore saves businesses every day.
These aren’t “optional extras.” They’re foundational habits that keep your website safe long-term.
Final Thoughts: WordPress Security Is Easier Than You Think
You don’t need to be a developer.
You don’t need to understand code.
You don’t need a massive budget.
You just need clear, direct instructions for what to add to your wp-config.php and .htaccess files — and now you have them.
By implementing these hardening rules, your website becomes:
- Harder to hack
- Faster to load
- More stable
- More professional
- Better protected than most business sites online today
WordPress security is not about fear. It’s about responsibility — and giving your business the protection it deserves.